KeePass: The Ideal Combination of Security and Convenience
Applying lessons from XKCD, the Iraq war, and recent cyberattacks to choose the best tool to safeguard your sensitive data.

A KeePass file encrypted with a strong password offers the best protection for your sensitive data in terms of convenience and strength-to-value ratio.

You Need a Password Manager
The most important thing you can do to protect your most valuable accounts is to avoid password reuse.
A picture is worth a thousand words:

Hopefully, that comic alone is enough to convince you that you need to create unique passwords for your accounts.
The question now becomes how do you store all those passwords?
The answer: a password manager. But which one?
Before we tackle that, we need to briefly discuss the strength-to-value ratio.
What is a "Strength-to-Value" Ratio?
In the military, one of the most useful ways to think about potential targets–both your own and the enemy's–is in terms of their strength-to-value ratio.
The ideal target for an attacker is one that has high value but is weakly defended.
A Brief Story Illustrating the Concept
I served two yearlong deployments to Baghdad, Iraq, as a young officer in the US Army.
I arrived in May of 2003, shortly after the swift collapse of the Iraqi army. The main threat to our forces was a simmering insurgency. In the beginning, the insurgents concentrated their efforts on attacking their highest value targets: US soldiers.
But they ran into a major problem: US soldiers are exceptionally-well trained and equipped. We were the very definition of a hard target.
The insurgents tried several tactics with varying degrees of success: improvised explosive devices (IEDs), vehicle-borne IEDs (VBIEDs), mortars, and rocket fire.
Mortars–basically rockets launched in a high arc by dropping them into a metal tube–would normally be an effective attack against a stationary, well-defended target, such as a US Army forward operating base (FOB). To be most effective, though, indirect fire attacks (like mortars) require a forward observer to relay back to the firing team instructions to fine tune the trajectory and zero in on the intended target.
The problem? The US Army has ground radar that detects the launch of such indirect fire attacks and can have rounds downrange–pinpointed at the source of the launch–before the original projectiles have even landed. The insurgents learned quickly that you didn't want to hang around after launching a mortar. In fact, they developed a technique where they would freeze the mortar rounds in a block of ice, aim the tubes at an Army FOB, and then vacate the area. When the ice melted in the hot Iraqi sun, the projectile would slide down the tube and launch itself without the need of a human operator.
While this sort of cat-and-mouse game played out in various ways at the tactical level over the course of the conflict, the insurgents also adapted at the strategic level.
Rather than continue to throw all their resources at the hardest targets, they went looking for softer targets instead. The result? A concerted effort to launch terror attacks against large gatherings of Iraqi civilians and civilian infrastructure, often in the form of terrorist bombings of mosques and power and water utilities. Their message to the Iraqi populace was this: as long as the US Army occupies this country, civilians will die and your life will be hard.
So, while the US Army remained the highest value target for the insurgents, the cost of attacking it was often not worth the payoff. Their solution was to attack softer civilian targets, extracting "value" by using the attacks to incite populist anger against the ongoing occupation.
Strength-to-Value Ratio of Password Managers
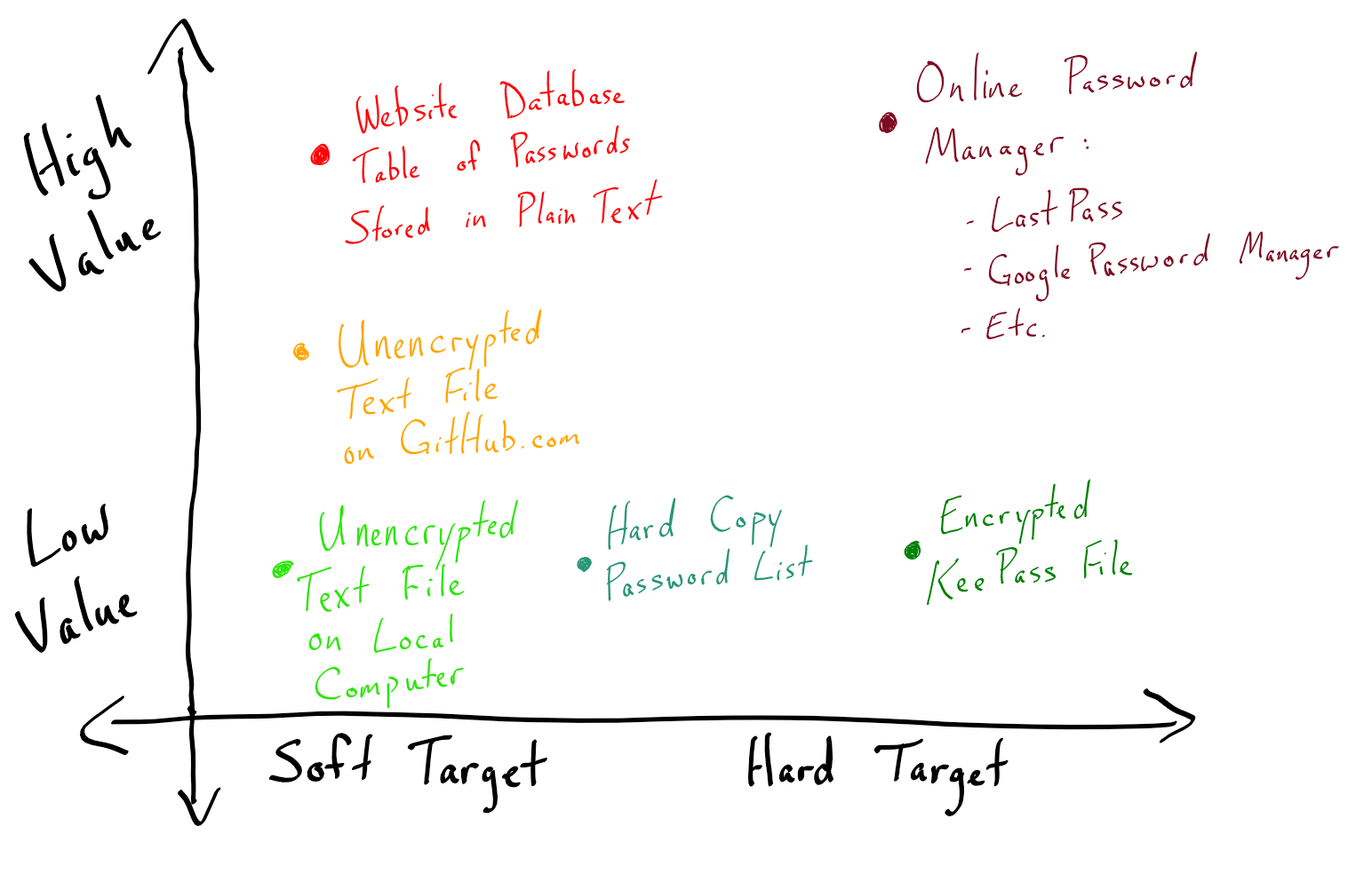
Off the top of my head, I came up with the following chart to help illustrate where various password managers fall in terms of the strength-to-value ratio.
The chart includes six examples (it is meant to be illustrative, not exhaustive):
- Online Password Managers
- Database of Plain-Text Passwords
- Unencrypted Text File Stored Online
- Unencrypted Text File Stored Locally
- Hard-Copy Password List
- Encrypted KeePass File
Online Password Managers
Online password managers, such as LastPass, offer convenience and extensive security.
They are the password manager equivalent of the US Army: a high-value, hard target.
They face a paradox from which they have no escape: the better they are at providing security and convenience, the more users they will accumulate. The more users they accumulate, the higher their value as a target. The higher their value as a target, the higher the payoff for a successful attack. The higher the payoff for a successful attack, the more resources an attacker will be willing to spend.
And, inevitably, a target with that much value will eventually be breached:
“This was accomplished by targeting [a] DevOps engineer’s home computer and exploiting a vulnerable third-party media software package, which enabled remote code execution capability and allowed the threat actor to implant keylogger malware,” LastPass wrote in an account of the situation. “The threat actor was able to capture the employee’s master password as it was entered, after the employee authenticated with MFA, and gain access to the DevOps engineer’s LastPass corporate vault.”

Database of PlainText Passwords
Passwords should never be stored in plain text.
In the early days of the internet, if you forgot your password, companies would email it to you so that you could log in again. If a company emails you a plaintext password that you created in the year of our Lord 2024, they are doing more things wrong than can be counted on a single human hand.
There is no need to store a plain text password.
The proper way to store a password is to perform a one-way hash of the password and store that instead. When a user signs in, they enter their password in plaintext, you perform the same one-way hash, and then compare the two hashes to make sure they match.
And while we're on the subject, you don't just store the hash of the plaintext password. You first salt the hash, so that if an attacker does gain access to your database of passwords, they can't perform a rainbow attack against the database to easily extract well-known passwords. The salt can be stored in plain text, but it must be a different randomly generated string for every record or it's essentially useless.
Most modern web frameworks provide built-in authentication methods that implement these best practices for you. Use them.
And whatever you do, DO NOT STORE PLAINTEXT PASSWORDS IN DATABASES:
During a sweep of the internet that took two weeks, the researchers scanned over five million domains connected to Google’s Firebase platform.
The total amount of exposed data is huge:
• Names: 84,221,169
• Emails: 106,266,766
• Phone Numbers: 33,559,863
• Passwords: 20,185,831
• Billing Info (Bank details, invoices, etc): 27,487,924
And as if that isn’t bad enough, 19,867,627 of those passwords were stored in plaintext. Which is a shame given that Firebase has a built-in end-to-end identity solution called Firebase Authentication that is specifically designed for secure sign-in processes and does not expose user passwords in the records.
So, an administrator of a Firebase database would have to go out of their way and create an extra database field in order to store the passwords in plaintext.
The researchers have warned all the affected companies, sending 842 emails in total. Only 1% of the site owners replied, but about a quarter of them did fix the misconfiguration.

Unencrypted Text File Stored Online
One of the least secure ways to store your sensitive data is in an unencrypted text file out in the cloud.
I know what you're thinking. Who would actually do that? Off the top of my head, I can think of at least 1.8 million people:
GitHub users accidentally exposed 12.8 million authentication and sensitive secrets in over 3 million public repositories during 2023, with the vast majority remaining valid after five days.
This is according to cybersecurity experts at GitGuardian, who sent out 1.8 million complimentary email alerts to those who exposed secrets, seeing only a tiny 1.8% of those contacted taking quick action to correct the error.
The exposed secrets include account passwords, API keys, TLS/SSL certificates, encryption keys, cloud service credentials, OAuth tokens, and other sensitive data that could give external actors unlimited access to various private resources and services, leading to data breaches and financial damage.

Unencrypted Text File Stored Locally
No, an unencrypted text file stored on your local computer is not inherently more secure than one stored on GitHub. But it sure is a lot harder for an attacker to find. And there is real value in that.
While security by obscurity is no replacement for actual security, there's a reason militaries design defenses with both cover and concealment in mind:

Hard-Copy Password List
It's time to stop making fun of your grandma for her yellow legal pad full of user names and account passwords that she keeps in the desk drawer next to her computer.
Unless your cousin has a side hustle stealing online identities for a Chinese cybercrime syndicate, that's probably one of the safest ways to store a list of passwords.
There's a reason the Russian government has been buying up manual typewriters to avoid storing secrets in any sort of digital format.

Encrypted KeePass File
And that brings us to the bottom-right corner of the Strength-to-Value ratio chart: an encrypted KeePass database file.
A single KeePass file combines the strength of an online password manager, but without the baggage of being a hugely valuable target to state-level cyber attackers. Use a very long master password (mine is 27 characters) that you will never forget. You might also want to physically write it down somewhere and store it in a safe place where a spouse or business partner can access it in case anything happens to you.
Store the file on a secure file-sharing service, such as OneDrive, Dropbox, or Box, and you have most of the convenience of LastPass with the added safety of relative anonymity.
Of course, if you happen to be a high-value target yourself (like, say, a US Secretary of State with a private email server or a DevOps engineer at LastPass), you still need to be wary of sophisticated targeted attacks. But for the rest of us peons? We generally need not worry ourselves with spearphishing campaigns that install keyloggers and extricate our private files.
While I'm sure there are better getting started guides for KeePass online, this one provides you with the basics:
The Bottom Line
A KeePass database with a strong password stored in a private cloud-based file-sharing service is the best combination of security and convenience for your sensitive data.




