Yes, VBA-Enabled Office Docs are a Significant Threat
VBA-enabled documents are commonly used to open the door for more virulent malware.

As I wrote about recently, Microsoft will begin blocking VBA macros in Office documents downloaded from email or the internet.
Understandably, this has caused quite a stir among Microsoft Access developers, not to mention the broader VBA development community. The new restrictions will make it harder for users to run Office documents with legitimate VBA code if they get those documents via email or the web. This is by design.
... and ...
It's the right decision by Microsoft.
Office Documents with VBA Macros are a Substantial Threat
According to Kevin Beaumont, former Microsoft employee and cybersecurity expert,
"Macros account for about 25% of all ransomware entry."
Kevin chose his words carefully there. The operative word in his quote is, "entry." Very little actual ransomware is written in VBA. Rather, VBA's role is to open the door for the ransomware executable to come inside.
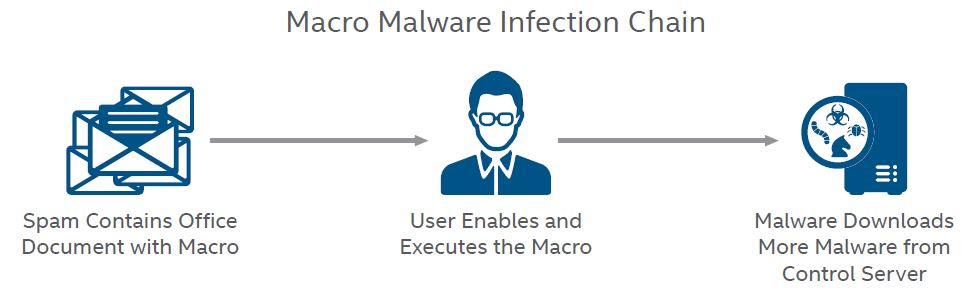
A great deal of modern ransomware uses the following approach:
- Email an infected Office document (Word, Excel, etc.) to an employee
- Convince employee to open document and enable macros
- Use embedded VBA to download malware from internet
- Run actual malware program written in C or C++
- Extort large sums of money from compromised organization
Here's a handy infographic from fossbytes.com:
Why VBA as a Malware Delivery Tool?
Years of telling users to NEVER run an application that someone emails to you–plus the fact that email clients and servers almost universally block the download and/or attachment of executable files–means that it's close to impossible for an attacker to deliver the actual ransomware software via email.
But, users get Office documents emailed to them all the time. Most of the time, it's perfectly safe to open them. This results in users being less suspicious of Office documents.
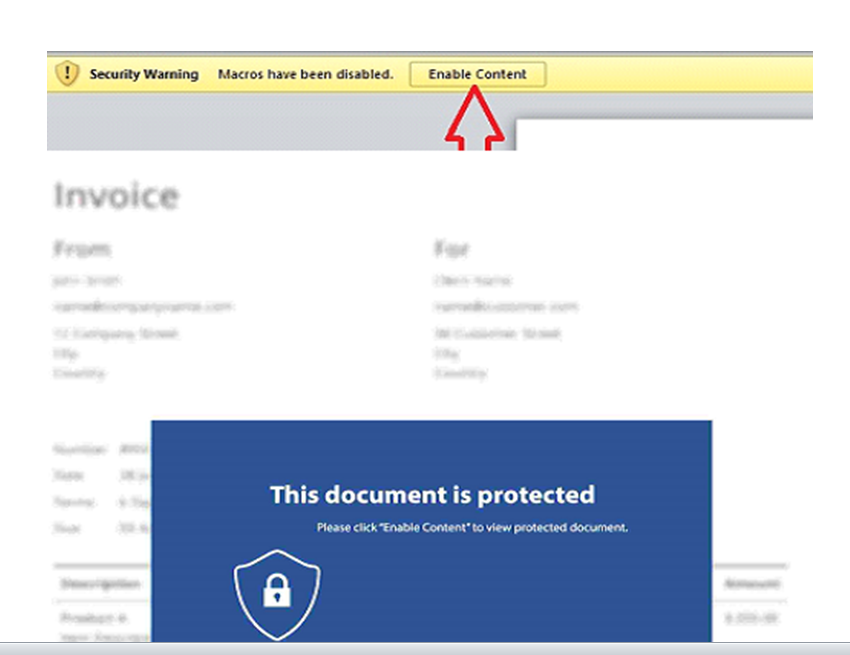
If you've spent any time working in information security, you know that the biggest vulnerability is almost always people. And modern-day social engineering techniques have come a long way since I first heard about the sudden passing of my long lost great uncle in Nigeria.
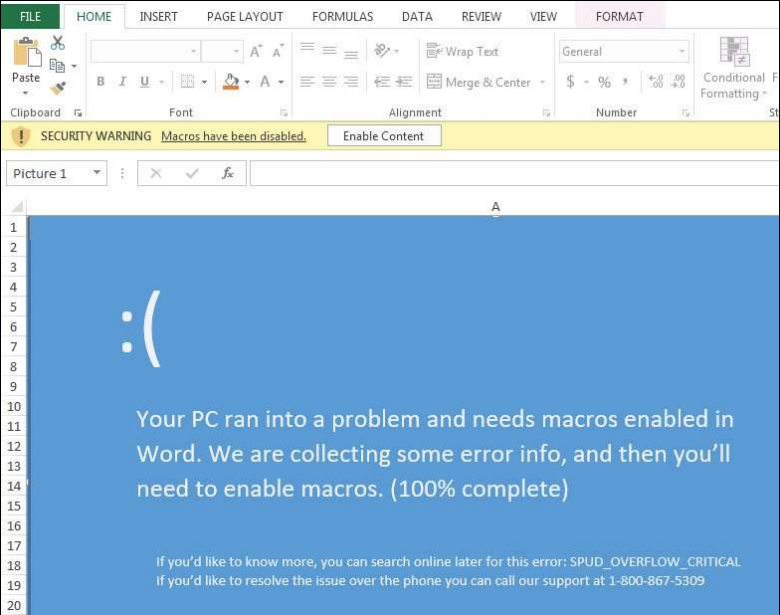
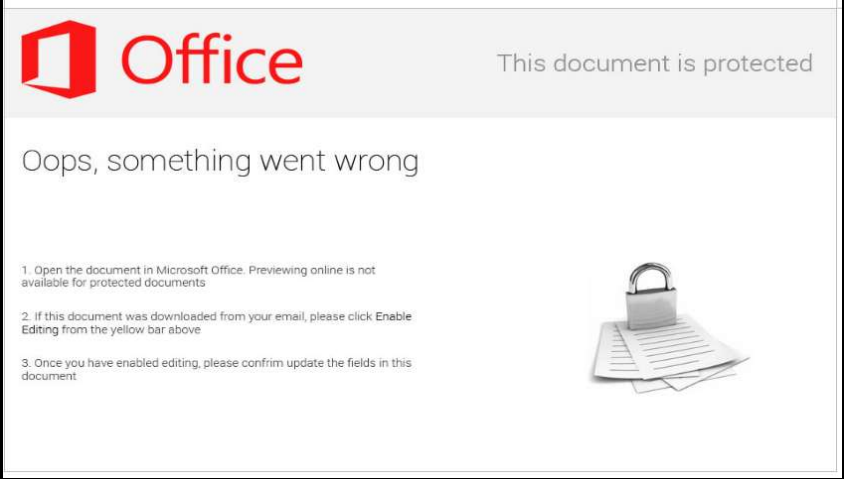
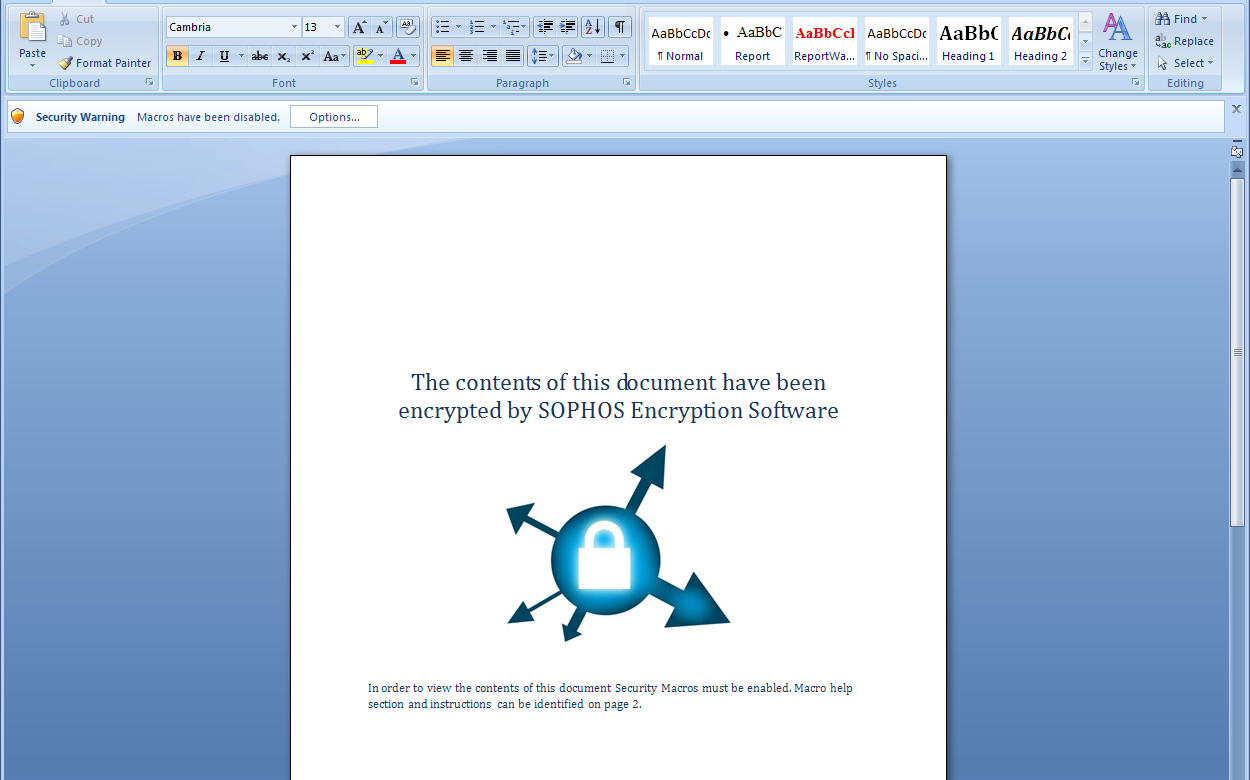
If you think the current yellow [Enable Macros] bar is sufficient, you may want to reconsider after seeing some of these devious subterfuges:

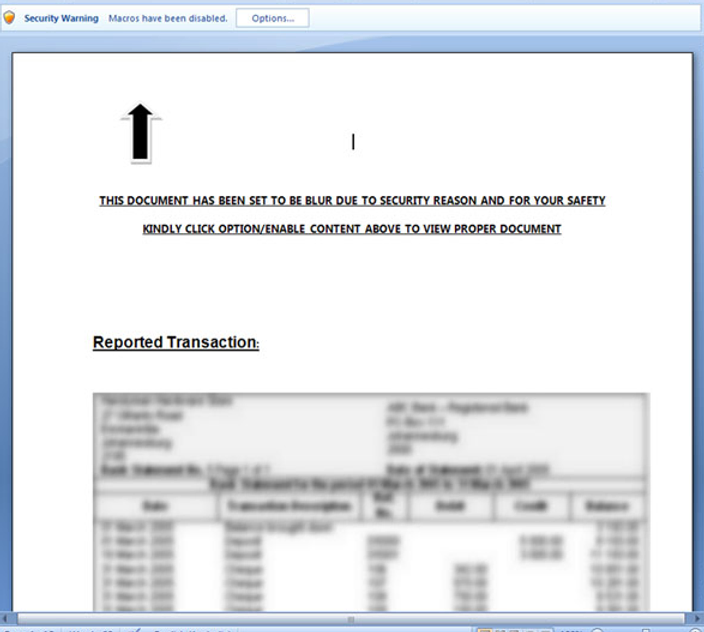
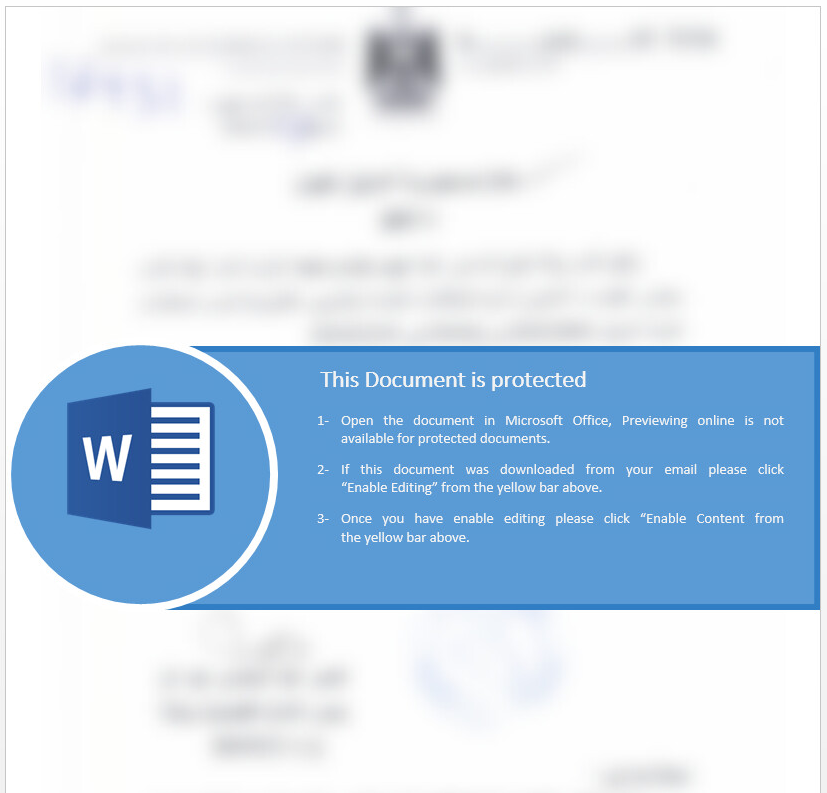
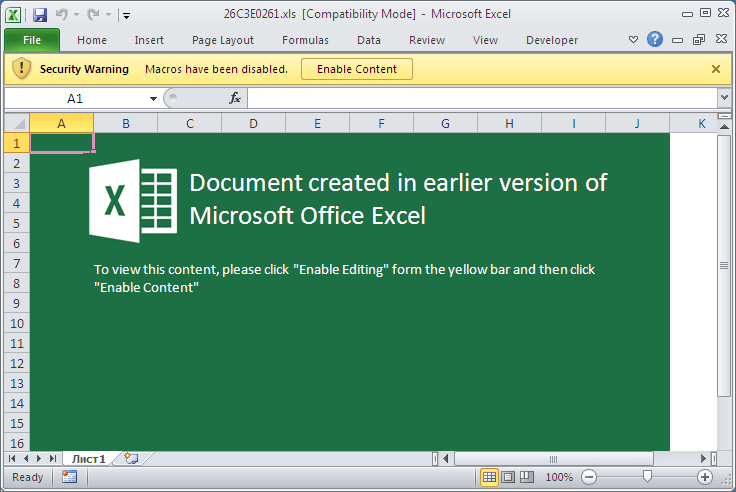
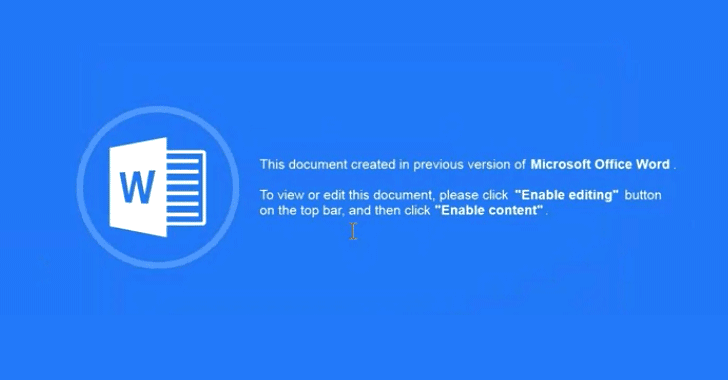
Referenced articles

External references







